Fraud: Part 1 - Who and how?
This post will delve into the world of fraud and internet
crime. I could probably type a hundred
pages on the subject; however I realize that’s not the best way to get
readers. I hope to provide you with
enough information to spark your interest and the resources to find out more
should you feel inclined. This particular
post will discuss internet crime trends and types of attacks. My next post will discuss the various types
of fraud and what you can do to protect yourself from the “bad guys”.
Who? - Cybercriminals
Unless you've been living under a rock, then you have
probably heard the terms cybercrime and cybercriminal. But how much do you really know about the
business of fraud? Crime, particularly
cybercrime, is a BIG business. It is
estimated that the cost of cybercrime in 2012 was $110 billion worldwide and
$21 billion in the United States1.
In fact, cybercrime is the new organized
crime that involves a complex business model and many intelligent players. In Russia, magazine publications on how to commit
fraud are sold in gas stations! And they,
the Russians, even hold seminars and classes on how to commit bank and card
fraud. The fraudster, or cybercriminal, will
steal the identity and/or financial information of an innocent person and then
use that identity and/or financial information to illegally obtain funds. Cybercriminals steal information from large
institutions by hacking into their networks or they steal information directly
from the victim’s computer. Stealing
directly from the victim is usually the preferred way because it is often
easier and less protected.
A recent investigation by RSA, discovered that
cybercriminals are using advanced web analytics tools and marketing techniques
to refine their attacks. By obtaining
statistics on their attacks, they are able to identify the most effective
attacks and the best time to conduct attacks.
For example, using web analytics and A/B testing, a cybercriminal can
determine which phishing email got the highest open rates and most
click-throughs2.
Often, what is most surprising to people, is how difficult
these criminals are to prosecute. Many
of the crimes are committed on computers in other countries, making prosecution
next to impossible (and that’s if you ever find the bad guy). To help law enforcement and regulatory
agencies organize their investigations, the Internet Crime Complaint Center, or
IC3, was established as a partnership between
the Federal Bureau of Investigation and the National White Collar Crime
Center. I won’t go into detail about
what they do, but in a nutshell, they enable consumers and businesses to report
cybercrime to a centralized place. Below
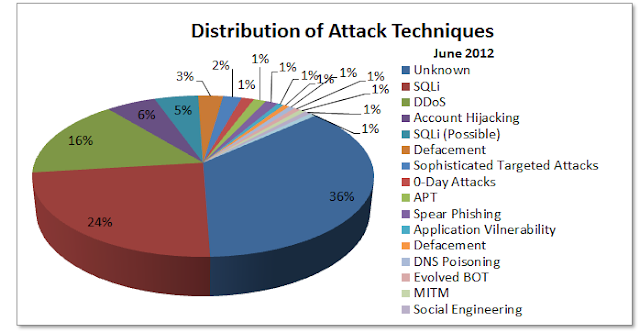
is a chart that shows the number of complaints the IC3 has received by year3:
Click here
to view the 2012 Norton Cybercrime Report for more facts about cybercrime.
How? - Types of Attacks
As I mentioned above, the first step in committing cybercrime
is to steal personal information. There is
an extensive black market that exists where cybercriminals buy and sell stolen personal
information over the internet. These online
Fraud Forums are used to exchange goods and services and are a way for
fraudsters to collaborate and offer up their skills and expertise4. If you've never googled “credit card dump”,
give it a try! There is a high-demand
for stolen information and the market is lucrative and pays well to those that
can obtain it. Cybercriminals use
extensive resources to obtain everything from card numbers, email addresses,
bank login information, to whole identities.
Once they have it, they sell the information to other cybercriminals who
then use it to steal money! It’s all
very exciting really.
Below I have described the most common attack techniques5
and 6:
· Malware
– Software that collects personal information from a computer undetected. Spyware, botnet, viruses, worms, keyloggers, Trojan
horses, adware, and more are all types of malware.
For more information on the types of attacks cybercriminals
use, click here.
I have included some resources below if you are interested
in reading more about cybercrime. My
next post, “Fraud: Part 2 – Why and what?” will discuss the other half of the
fraud business model. What do fraudsters
do with your personal information and what can you do to protect yourself from
them?
References and Resources
[1] http://now-static.norton.com/now/en/pu/images/Promotions/2012/cybercrimeReport/2012_Norton_Cybercrime_Report_Master_FINAL_050912.pdf
[2] http://searchsecurity.techtarget.com/answer/Use-cybercrime-statistics-to-combat-organized-cybercrime
[3] http://butleritsec.blogspot.com/2012/05/cybercrime-statistics.html
This post will delve into the world of fraud and internet
crime. I could probably type a hundred
pages on the subject; however I realize that’s not the best way to get
readers. I hope to provide you with
enough information to spark your interest and the resources to find out more
should you feel inclined. This particular
post will discuss internet crime trends and types of attacks. My next post will discuss the various types
of fraud and what you can do to protect yourself from the “bad guys”.
Who? - Cybercriminals
Unless you've been living under a rock, then you have
probably heard the terms cybercrime and cybercriminal. But how much do you really know about the
business of fraud? Crime, particularly
cybercrime, is a BIG business. It is
estimated that the cost of cybercrime in 2012 was $110 billion worldwide and
$21 billion in the United States1.
In fact, cybercrime is the new organized
crime that involves a complex business model and many intelligent players. In Russia, magazine publications on how to commit
fraud are sold in gas stations! And they,
the Russians, even hold seminars and classes on how to commit bank and card
fraud. The fraudster, or cybercriminal, will
steal the identity and/or financial information of an innocent person and then
use that identity and/or financial information to illegally obtain funds. Cybercriminals steal information from large
institutions by hacking into their networks or they steal information directly
from the victim’s computer. Stealing
directly from the victim is usually the preferred way because it is often
easier and less protected.
A recent investigation by RSA, discovered that
cybercriminals are using advanced web analytics tools and marketing techniques
to refine their attacks. By obtaining
statistics on their attacks, they are able to identify the most effective
attacks and the best time to conduct attacks.
For example, using web analytics and A/B testing, a cybercriminal can
determine which phishing email got the highest open rates and most
click-throughs2.
Often, what is most surprising to people, is how difficult
these criminals are to prosecute. Many
of the crimes are committed on computers in other countries, making prosecution
next to impossible (and that’s if you ever find the bad guy). To help law enforcement and regulatory
agencies organize their investigations, the Internet Crime Complaint Center, or
IC3, was established as a partnership between
the Federal Bureau of Investigation and the National White Collar Crime
Center. I won’t go into detail about
what they do, but in a nutshell, they enable consumers and businesses to report
cybercrime to a centralized place. Below
is a chart that shows the number of complaints the IC3 has received by year3:
Click here
to view the 2012 Norton Cybercrime Report for more facts about cybercrime.
How? - Types of Attacks
As I mentioned above, the first step in committing cybercrime
is to steal personal information. There is
an extensive black market that exists where cybercriminals buy and sell stolen personal
information over the internet. These online
Fraud Forums are used to exchange goods and services and are a way for
fraudsters to collaborate and offer up their skills and expertise4. If you've never googled “credit card dump”,
give it a try! There is a high-demand
for stolen information and the market is lucrative and pays well to those that
can obtain it. Cybercriminals use
extensive resources to obtain everything from card numbers, email addresses,
bank login information, to whole identities.
Once they have it, they sell the information to other cybercriminals who
then use it to steal money! It’s all
very exciting really.
Below I have described the most common attack techniques5
and 6:
· Malware
– Software that collects personal information from a computer undetected. Spyware, botnet, viruses, worms, keyloggers, Trojan
horses, adware, and more are all types of malware.
· Phishing
– An email, instant message, or other communication that appears to be from a
trustworthy source. The purpose of these
fraudulent communications is to obtain usernames, passwords, and card numbers.
· SQL Injections – A
technique often used to attack data driven applications. This is done by
including portions of SQL statements in an entry field in an attempt to get the
website to pass a newly formed SQL command to the database (e.g., dump the
database contents to the attacker).
· Denial-of-Service
– Flooding a network or server with traffic in order to make it unavailable to
its users. This enables the fraudsters
to redirect victims to a spoofed website in order to intercept their personal
information.
· Skimming
– Devices that steal credit card information when the card is swiped through
them. The stolen credit card information is then sold online through an online
action to carders
who use the numbers to make counterfeit cards.
For more information on the types of attacks cybercriminals
use, click here.
I have included some resources below if you are interested
in reading more about cybercrime. My
next post, “Fraud: Part 2 – Why and what?” will discuss the other half of the
fraud business model. What do fraudsters
do with your personal information and what can you do to protect yourself from
them?
References and Resources
[1] http://now-static.norton.com/now/en/pu/images/Promotions/2012/cybercrimeReport/2012_Norton_Cybercrime_Report_Master_FINAL_050912.pdf
[2] http://searchsecurity.techtarget.com/answer/Use-cybercrime-statistics-to-combat-organized-cybercrime
[3] http://butleritsec.blogspot.com/2012/05/cybercrime-statistics.html
[4] http://www.firstdata.com/downloads/thought-leadership/fraudtrends2010_wp.pdf
[5] http://www.carnegiecyberacademy.com/facultyPages/cyberCriminals/operate.html#techniques
[6] http://www.firstdata.com/downloads/thought-leadership/fraudtrends2010_wp.pdf
http://hackmageddon.com/2012/07/13/june-2012-cyber-attacks-statistics/
http://www.businessweek.com/articles/2012-08-02/the-cost-of-cyber-crime
http://news.techworld.com/security/3403711/rsa-cybercriminals-plot-massive-banking-trojan-attack/
www.fbi.gov
www.ic3.gov
www.ice.gov

Great info! This post goes along with many realting to social media in the many dangers of revealing too much info online. Many people reveal their date of birth on social networking sites and have no idea how dangerous that is (for financial crimes/ identity theft).
ReplyDeleteWe just talked about some of this stuff in the Networking and Servers class but analytics tools weren't mentioned at all. It's interesting how creative these people can be and how useful tools for improving your business can become useful for criminals as well.
ReplyDeleteIn addition to people revealing too much personal information online, many software vendors are collecting more and more personal data for authentication purposes. Some social websites require cell phone number to authenticate the user before log in. We can only hope security effectiveness stay proportionate to the threats.
ReplyDelete